The Security Consultants
The fight against online crime is an increasingly common problem. The most frequently encountered threats include: malware, cybersquatting, blacklisting, phishing, traffic diversion, identity theft, loss of sensitive data, and much more.
I help companies maintain their online Business Continuity. Through our consultants and market-leading partners, we continue to offer a wide range of customized security solutions and services. Issues on your website can seriously compromise your business and corporate reputation, which is why I have developed a range of specific services to ensure complete protection of your online presence.
These services are part of a cycle called ONLINE BUSINESS CONTINUITY.
New services with accredited Pentester activities:
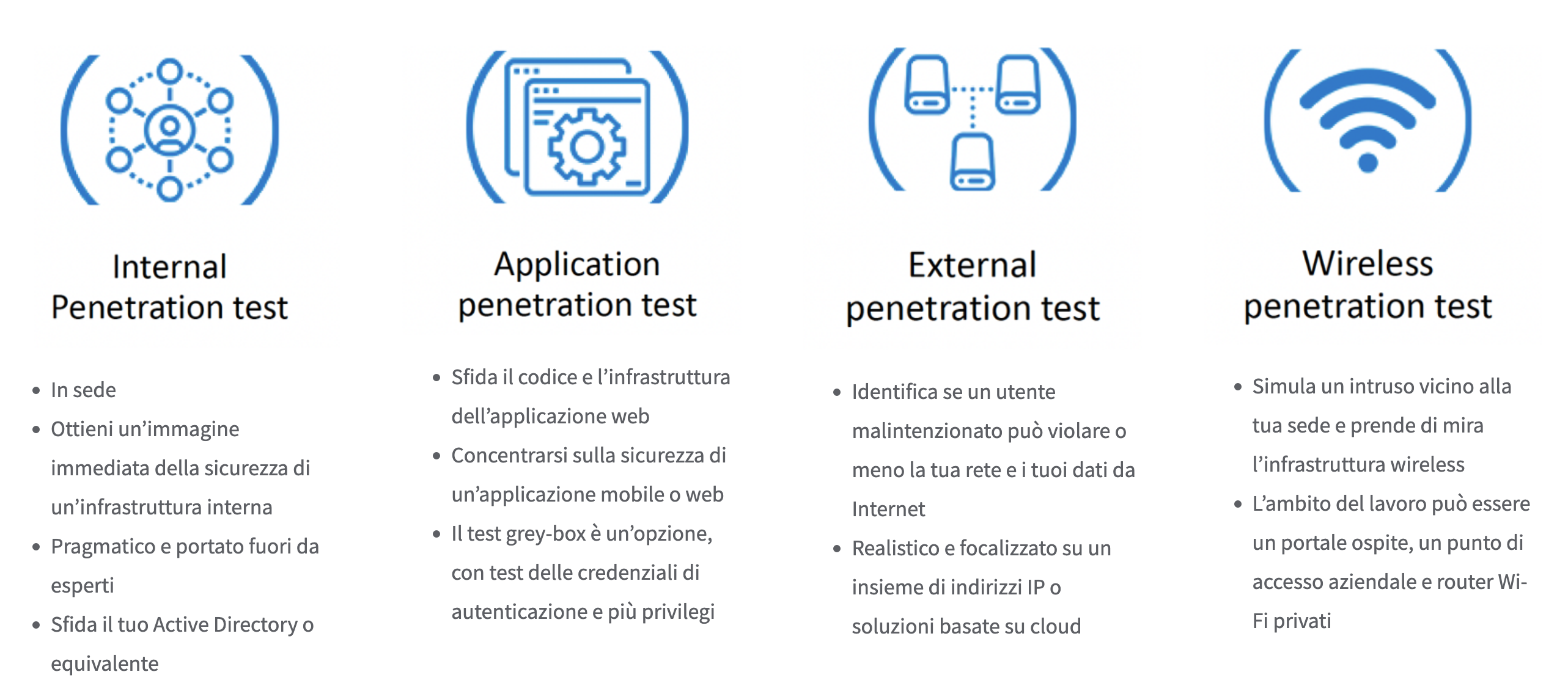
- Internal and External Penetration Testing;
- Application Penetration Testing;
- Wireless Penetration Testing;
- Red Team;
- Phishing Attack;
- Password Audit;
- Incident Response;
- Vulnerability Assessment.
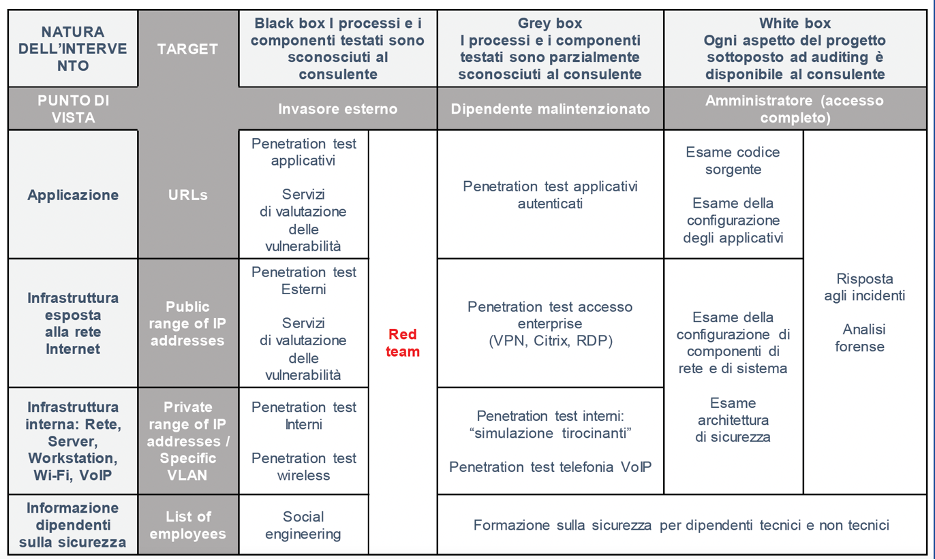
The penetration testing and auditing services offered are the best way to examine and evaluate the internal and external security of a company’s IT systems.
A penetration test is a simulated hacker attack on a computer system, network, or organization under real conditions. It helps determine how resistant your IT system is to real threats.
Security audits complement penetration tests by adding an extra layer of evaluation regarding technical aspects such as source code, system configuration, network setup, and other documentation that an intruder typically doesn’t have access to
For each of these services, we provide detailed Reports containing a technical summary of vulnerabilities and remedies to be implemented, as well as details about the attempts made by experts and the positive security aspects identified during the test.
Penetration testing services
Our commitments