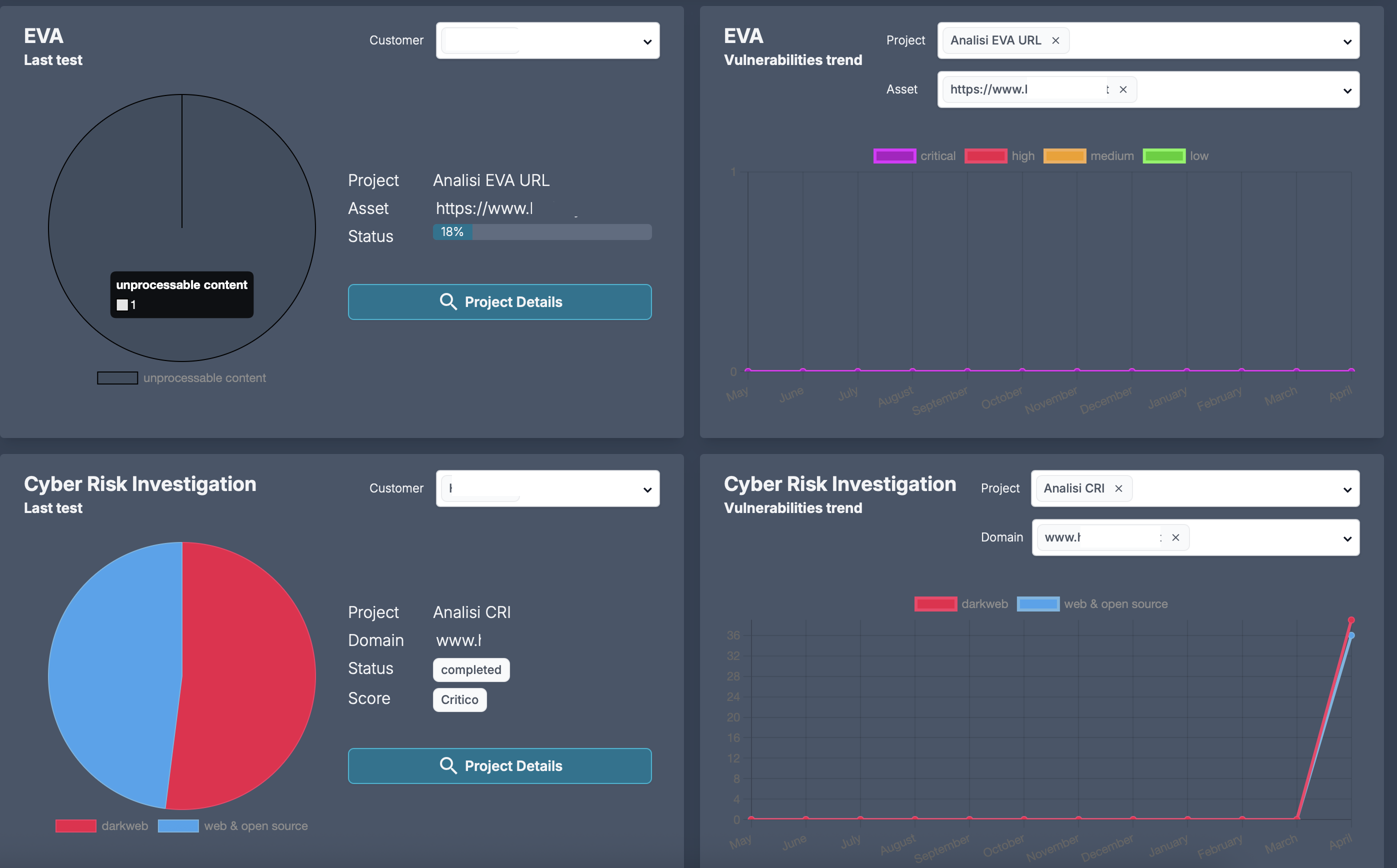
The Cyber Risk Investigation (CRI)
The Cyber Risk Investigation (CRI) is the service that helps companies identify, monitor and mitigate IT risks without performing invasive tests on their infrastructure.
Thanks to advanced Threat Intelligence, CRI collects and analyzes data from public sources, deep web and dark web, offering a clear and updated view of the company’s exposure to potential attacks. This approach allows for the detection of compromised credentials, data breaches, exposed information and malicious activities that could be exploited by cybercriminals.
CRI is not limited to static analysis: it provides real-time updates and allows for in-depth investigation of identified threats with the support of an Ethical Hacker, transforming prevention into a strategic advantage.
CRI performs an in-depth scan of multiple web levels to identify potentially
dangerous information:
- OSINT (Open Source Intelligence): publicly accessible information, such as disclosed data breaches, forums, code repositories, social media and exposed documents.
- Deep Web: content not indexed by traditional search engines, such as databases accessible with credentials or cloud archives without adequate protection.
- Dark Web: illegal markets, hacker forums, leak repositories and other sources where stolen data and tools for cyber attacks are bought and sold.
The Cyber Risk Investigation (CRI) is an essential solution for those who want to anticipate cyber attacks and reduce business risks.
With continuous monitoring and a data-driven approach, companies can strengthen their security, protecting data, assets and reputation.
Don’t wait to suffer an attack: discover today the level of exposure of your company with CRI
What EVA does – Surface scan & enumeration
EVA’s surface analysis covers both the network and services aspects, from public IP addresses and web applications to internal corporate IT systems.
Once the target is obtained from the client, EVA performs a black-box analysis of possible attack points exploitable by a cybercriminal, optimizing its research through the determination and traceroute of the hosts used and the active services by the client (e.g., Apache, Solaris, Nginx, etc.).
EVA is able to recognize the types of devices used (e.g., routers, firewalls, DVRs, industrial machines, IP cameras etc.), identifies the versions of the operating system running (e.g., Windows, Linux through TCP/IP stack fingerprinting, SCADA) and the types of filters used by the IT system (e.g., IDS/WAF for monitoring anomalous activities on the network).
The software scans the protocols and services used (e.g., FTP, SSH, HTTP, WebDAV, etc.), identifies Common Platform Enumeration (CPE) and performs enumeration activities on the identified resources (e.g., NetBIOS, SNMP, LDAP, Kerberos, MySQL, PostgreSQL), extracting information such as service version, git commit, build date, auth permission, namespaces, pods
Exploitation (Penetration Testing)
EVA’s penetration testing activity has been developed in its proprietary code to have exploit mode by default, which allows for the identification and exploitation of known vulnerabilities (CVE exploits) following the enumeration activity of the analyzed hosts, without having a negative impact on the operability of the analyzed system.
EVA is able to generate so-called evasive payloads, i.e., those that aim to evade antivirus software (e.g., Windows Defender), without the need for external support from other tools, but in complete autonomy and in black box.
All vulnerabilities are verified and tested, where necessary and possible, to avoid impacting the performance of the analyzed systems. The exploitation tests cover the analysis areas post surface scanning, therefore they include, for example, testing of the application protocols used (e.g., HTTP, HTTPS), network files (e.g., SMB dumping, eternal blue), encryption protocols (e.g., SSH), JBoss server applications and more generally Java (e.g., deserialization, RMI over HTTP, Jenkins RCE, Remote JMX), databases (e.g., MySQL and Microsoft SQL Server brute force and dumping) and active directory in case of custom service.
Encryption test
EVA is able to perform an analysis of encryption settings and related vulnerabilities present on network resources (e.g., Lucky13, Sweet32, Poodle, Beast, etc.). During this activity, configurations related to the encryption protocol used are identified and any cryptographic defects present are identified, including those at the service level (e.g., HTTPS, STARTTLS for MySQL, PostgreSQL). During this activity, EVA connects to the server and analyzes its SSL/TLS configuration (including SSLv2, SSLv3 and TLS v1.3 versions), particularly searching for advanced encryption settings (e.g., certificates, cipher suites, elliptic curves, etc.) and ensuring that it is not vulnerable to known TLS
attacks (e.g., Heartbleed, ROBOT, OpenSSL CCS injection, etc.).
EVA is also able to perform more specific encryption analyses (e.g., base64, 3DES, RC4, DHE keys), with the objective of highlighting critical credentials, i.e., those that would allow an attacker to reach the most confidential corporate information.
OSSTMM Methodology
EVA follows the testing methodology described in the Open Source Security Testing Methodology Manual (OSSTMM), designed to test the operational security of workstations, workflows, wireless and data networks more generally. EVA has chosen to adhere to this framework as well because it is considered a technical reference supporting the ISO/IEC 27001 standard.
To this end, EVA is the tool for security analysis, which can be integrated into the company as an integral part of the workflow established in the OSSTMM model (cf., Chapter 6 – Work Flow, OSSTMM 3), precisely because it focuses on vulnerability research activities and verification of the robustness of the corporate IT system.
OWASP checklist
EVA follows the principles of the OWASP Testing Project, i.e., it performs its VA/PT activities according to the Penetration Testing Execution Standard (PTES), which defines the test path in 7 phases:
1. Pre-engagement interactions
2. Information gathering
3. Threat modeling
4. Vulnerability analysis
5. Exploitation (where possible)
6. Post-exploitation analysis
7. Report
ISO 27001
EVA has set up its testing activities to support companies in being compliant with the new ISO/IEC 27002:2022 standard, which has a new structure and involves an important modification of ISO/IEC 27001:2013, particularly to realign Annex A. Indeed, the new standard requires that controls be more substantial and performance-related, i.e., focused on cyber prevention.
Don’t wait to suffer an attack: discover today the level of exposure of your company with EVA