IT consultation for secure management of company resources and data EU 2016/679 and Legislative Decree 101/2018
Information security is the area of computer science that deals with safeguarding systems from potential risks and/or data breaches, analyzing vulnerabilities, threats or attacks, and thus protecting the physical integrity (hardware) and logical-functional integrity (software) of an IT system and the data contained in it or exchanged in communication with a user and on the Internet
There are Risks not Worth Taking!
Would you hand your computer over to a scammer? And would you give them free access to your emails, your clients’ private data, all your accounting, confidential information, passwords (including those for the bank), and your card PINs?
IT’S A SERIOUS MISTAKE TO THINK “…IT WON’T HAPPEN TO ME!“
If you’re not really protecting yourself from cyber attacks, you’re taking a huge risk! And don’t think “…it won’t happen to me,” because that’s exactly what thousands of defrauded Italians thought before they saw their business and life ruined.
2021 will predictably also lead to an increase in attacks targeting personal/home devices and home networks often used by multiple family members. Hackers/cybercriminals, for example, could target relatives and exploit their devices as a “bridgehead” to reach corporate networks.
Protecting your data is a legal obligation, but even more so a duty towards the security of your business and your loved ones. Don’t be caught unprepared.
Online Editorial 
Book now by calling
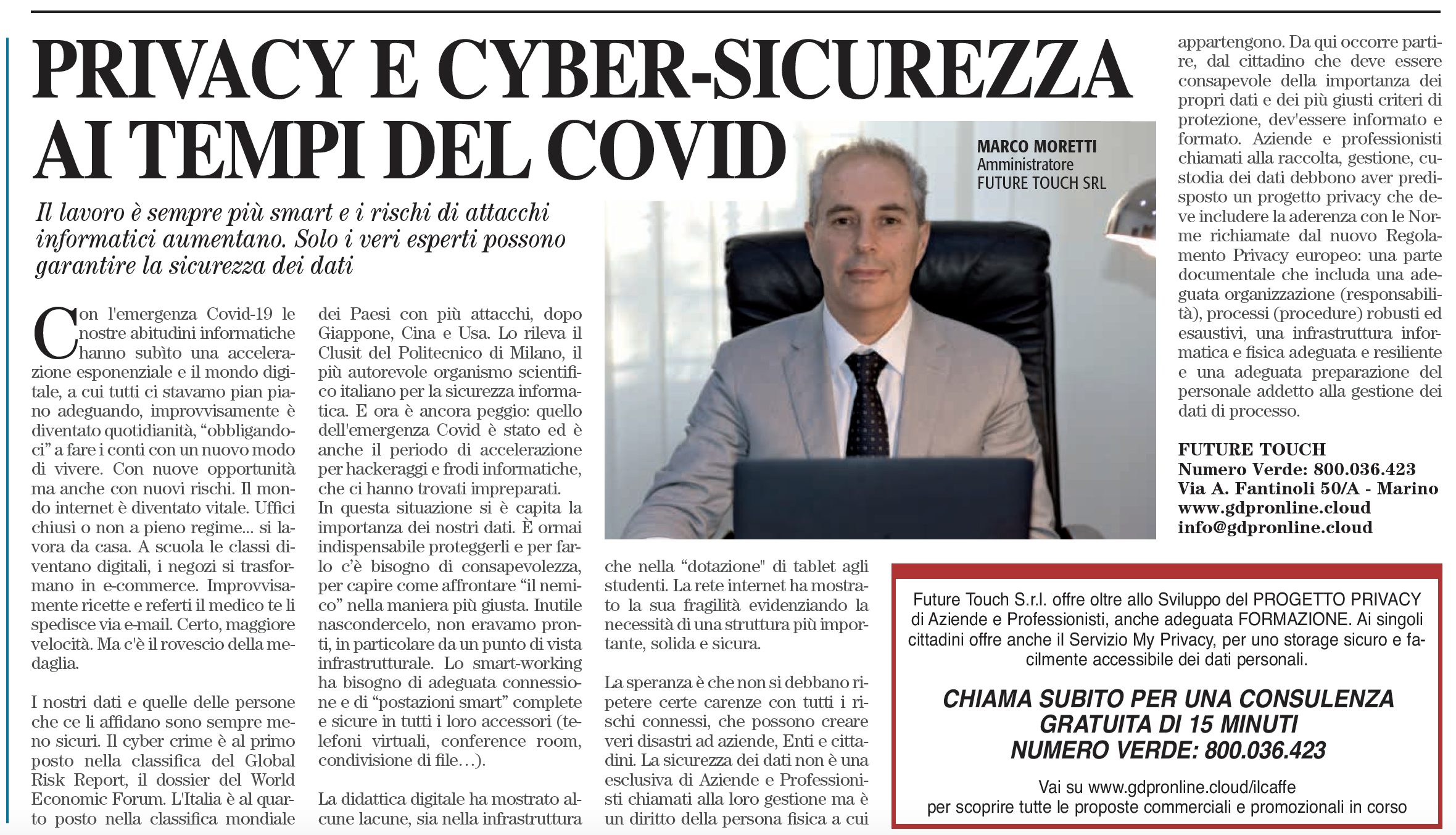
Privacy and Cyber Security in the Time of Covid
August 2020 Editorial “Il Caffè”
My activity consists of implementing such protection through technical-organizational and functional measures aimed at ensuring:
• the correctness of data (integrity);
• the confidentiality of data (encryption);
• physical and/or logical access only to authorized users (authentication);
• the use of all and only the services provided for that user in the times and ways provided by the system
• protection of the system from malicious software attacks to guarantee the previous requirements.
Examples of some Consulting activities:
- Risk analysis
- Security measures
- Passive security (physical security)
- Active security (data and program security)
- Security in companies, application of ISO 27001:2005 standard
- Data security
- Undesired events
- Accidental events
- Program security
- Transmission and telecommunications security
- Internet network security
- Corporate local network security; Firewall; Intrusion detection system (IDS-IPS)
- Certification on third-party devices and software applications
- GDPR Privacy Consultation Legal DPO/RPD and IT Assessment
The GDPR is the set of RULES that govern the processing and circulation of personal data of natural and legal persons, i.e., citizens, organizations, and companies. The new regulation puts the individual at the center of the project as each of us is the main source of data collection for many companies that use our consent for the provision of certain services.
The new regulation indicates the correct methods for data processing, starting from the common citizen and indicating how their data should be processed, their rights and how to enforce them, up to indicating precise rules and technical disciplinary measures that every company, entity or professional must adopt to comply with the new regulation and the processing of data of people who interact with the company, employees, suppliers, collaborators, customers.
Request a free evaluation on the portal dedicated to the service www.gdpronline.cloud
DPO/RPD GDPR Privacy Guarantor Certificate (G. Marconi University)
IT Consultation for the Right to be Forgotten and Online Reputation
Source: https://it.wikipedia.org/wiki/Sicurezza_informatica